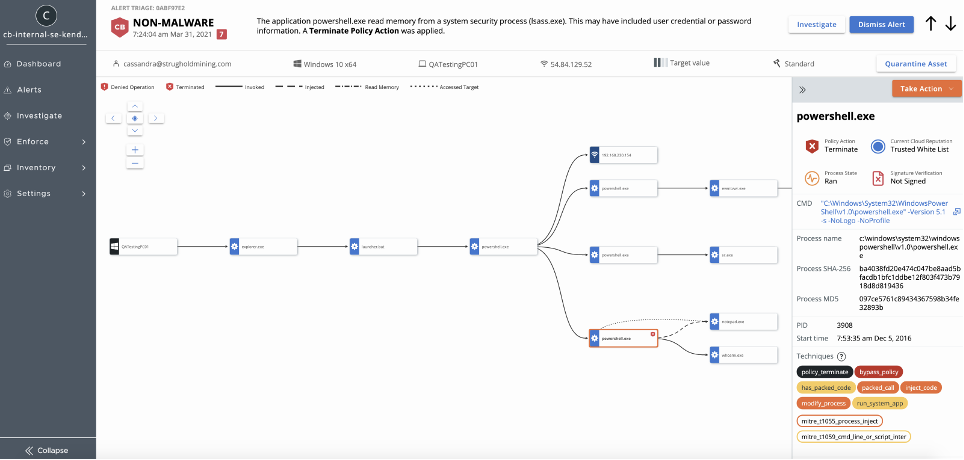
The Ultimate Carbon Black EDR Admin Guide: A Step-by-Step Tutorial for Effective Endpoint Security
Carbon Black is one of the most popular endpoint security solutions on the market. If you’re looking for a comprehensive guide to configuring and managing Carbon Black EDR, you’ve come to the right place.
In this article, we’ll walk you through everything you need to know about Carbon Black EDR, from installation to daily administration tasks. By the end of this guide, you’ll be an expert in using Carbon Black EDR to protect your endpoint devices from threats.
So let’s get started!
Table of Contents
Getting Started with Carbon Black EDR
Configuring and Managing Carbon Black EDR
Carbon black edr tips and tricks
Conclusion
Getting Started with Carbon Black EDR
If you’re looking for a comprehensive guide to Carbon Black EDR, look no further! In this blog article, we’ll walk you through everything you need to know about getting started with Carbon Black EDR, including a step-by-step tutorial for effective endpoint security.
We’ll cover the following topics:
What is Carbon Black EDR?
Why use Carbon Black EDR?
How to get started with Carbon Black EDR?
What are the benefits of using Carbon Black EDR?
By the end of this blog article, you’ll have a clear understanding of how to get started with Carbon Black EDR and how it can help improve your endpoint security. So let’s get started!
Configuring and Managing Carbon Black EDR
In this section, we’ll cover the basics of configuring and managing Carbon Black EDR. First, we’ll go over the various settings that can be adjusted in the console. Next, we’ll cover how to deploy agents to endpoints. Finally, we’ll show you how to create and manage policies.
Settings: The first thing you’ll want to do is log into the console and click on the “Settings” tab. From here, you can adjust several different options including the alarm sensitivity, logging level, and whether or not you want to receive email notifications.
Deploying Agents: To deploy agents to endpoints, click on the “Agents” tab and then select the “Deploy Agents” option. You will then be prompted to enter in the IP addresses or hostnames of the endpoints that you wish to deploy to. Once the agent has been deployed, it will automatically start collecting data from the endpoint.
Policies: Policies are used to define what actions should be taken when certain events occur on an endpoint. To create a policy, click on the “Policies” tab and then select “Create Policy.” You will then be prompted to enter in a name for the policy as well as a description of what it does. After creating a policy, you can then assign it to one or more endpoints by clicking on the “Edit” button next to an endpoint’s entry in the console.
Carbon black edr tips and tricks
When it comes to carbon black edr, there are a few tips and tricks that can make your experience more effective. Here are some of our top suggestions:
Download the latest content updates regularly. This ensures that you have the most up-to-date information to work with, and helps keep your environment consistent.
Use the enrichment capabilities wisely. Enriching data can provide valuable context and help you better understand what’s happening on your endpoints.
Create custom responses for each endpoint group. This allows you to tailor your response to the specific needs of each endpoint, and provides greater flexibility overall.
Take advantage of playbooks. Playbooks allow you to automate certain tasks, which can free up time for other priorities.
Keep an eye on dashboards and reports. These tools can help you quickly identify areas of concern, and track your progress over time.
Conclusion
Carbon Black EDR is a powerful tool that can be used to protect your endpoints from cyber threats. With this comprehensive guide, you now have the knowledge and skills to configure, manage and monitor your Carbon Black EDR environment in an effective manner. Whether you are a novice or an experienced administrator, we hope our step-by-step tutorial will help make managing endpoint security easier for you.



