
How to Recognize a Ransomware Attack
In the rapidly evolving digital landscape, being able to recognize the warning signs of a potential ransomware attack is crucial. Ransomware attacks have seen a sharp rise, causing significant damage to individuals and businesses alike like online casinos . This blog post aims to shed light on the key indicators that can help you identify an impending ransomware attack, empowering you to take proactive measures and protect your digital assets.
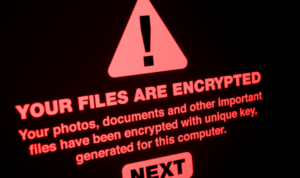
Unexpected Pop-ups and Messages
One of the most conspicuous signs of a ransomware attack is encountering unexpected pop-ups or messages on your device. These messages often convey threats or demands for payment, hinting at an ongoing or imminent attack. Pay close attention to any sudden, unsolicited messages that demand actions from you.
Sudden Encryption of Files
If you notice that your files are becoming inaccessible or have strange file extensions, your system might be under a ransomware attack. Ransomware encrypts files, making them unusable, and then demands payment for decryption. If you find yourself unable to open your files or if file icons appear different than usual, it’s a red flag signaling a potential ransomware attack.
Unusual Network Activity
Monitoring your network activity is crucial in identifying potential ransomware attacks. If you observe unexpected high network usage, especially when your system is idle, it could be indicative of ransomware attempting to communicate with its command and control server or encrypting your files in the background. Any unusual network behavior should be investigated immediately.
Changes in File Extensions
A significant ransomware attack indicator is a change in file extensions. When ransomware encrypts your files, it often alters their extensions to something uncommon or random. If you notice this alteration in your file extensions and you did not make any changes yourself, it’s a clear signal that your system is under a ransomware threat.
Disabled Security Software
Ransomware often attempts to disable your security software to carry out its malicious activities without interruption. If you find that your antivirus or other security programs have been unexpectedly turned off or altered without your consent, it could be a ransomware attack in progress.
Missing or Altered Files
Another critical warning sign is discovering missing or altered files, especially in crucial system directories. Ransomware often targets important files, making them disappear or modifying them to disrupt system functionality. If you notice sudden alterations or disappearances of essential files, it’s a strong indicator of a ransomware attack.
Unexpected Account Activities
Keep an eye on your financial accounts and email accounts for any unanticipated activities, such as unauthorized transactions or changes in passwords. Ransomware attackers may attempt to exploit your accounts during an attack. If you spot any suspicious activities, act swiftly to secure your accounts and investigate the cause.
Presence of a Ransom Note
Ransomware attacks typically come with a ransom note, either displayed on your screen or left in affected folders. This note outlines the attacker’s demands and instructions for payment. If you find a ransom note on your device, it’s an obvious sign of a ransomware attack.
Phishing and Suspicious Emails
Phishing emails are a common entry point for ransomware. Be cautious of unexpected or unsolicited emails, especially those with suspicious attachments or links. Cybercriminals often use social engineering tactics to trick users into downloading malicious attachments or clicking on harmful links, leading to a ransomware infection.
Conclusion
Ransomware attacks can have severe consequences, both personally and professionally. Recognizing the warning signs and indicators of a ransomware attack is crucial in mitigating potential damage. Stay vigilant, educate yourself and your team, and implement robust cybersecurity measures to safeguard against the ever-evolving threat landscape.


