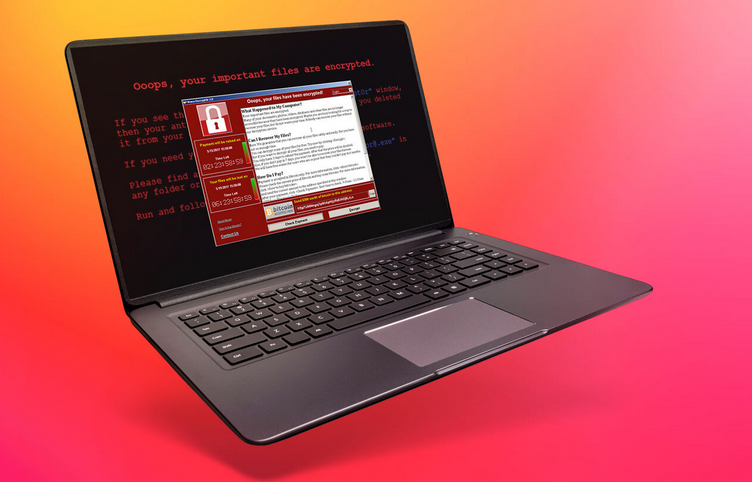
How to Tell If Your Files Have Been Encrypted by Ransomware
In the age of digital threats and cyberattacks, ransomware has emerged as a significant concern for individuals and organizations alike. Ransomware is a type of malware that encrypts your files, making them inaccessible until a ransom is paid to the attacker. Detecting a ransomware infection early is crucial to preventing data loss and financial damage. In this article, we will explore how to tell if your files have been encrypted by ransomware.

Unusual File Extensions
In the early stages of a ransomware attack, you’ll notice unfamiliar file extensions. The ransomware typically alters your file names by adding unique extensions, rendering them inaccessible. For instance, a file previously known as “document.pdf” could change to “document.pdf.locked” or adopt a different, unusual extension. Please visit best payout casinos in Australia and make extra money online.
Ransom Notes
Ransomware attackers want you to know that your files are encrypted, and they usually leave ransom notes on your computer. These notes may appear as text files or pop-up messages explaining the situation and providing instructions on how to pay the ransom. If you come across a ransom note, it’s a clear indication of a ransomware attack.
Inaccessible Files
When ransomware encrypts your files, it uses a strong encryption algorithm that renders the files inaccessible without the decryption key. If you attempt to open a file and receive an error message stating that the file is corrupt or cannot be accessed, there’s a high likelihood it has been encrypted by ransomware.
Changes in File Contents
Some ransomware strains don’t change file extensions but alter the contents of your files. You may notice that the content of your documents, images, or other files has been replaced with gibberish, and the files are no longer usable.
File Icons and Names
In some cases, ransomware may not change file extensions but can modify file icons and names. For instance, an image file may appear as a different file type, and the name could be altered to something random or include an added extension like “.encrypted” or “.locked.”
Ransomware Lock Screen
Certain types of ransomware display a lock screen when you attempt to access your computer. This lock screen usually features the ransom note, a countdown timer, and instructions on how to pay the ransom. If your computer suddenly presents a lock screen you didn’t set up, it’s a sign of a ransomware infection.
Encrypted File Markers
Some ransomware variants use markers within the file to indicate encryption. These markers are unique patterns of characters or codes placed at the beginning or end of encrypted files. If you inspect the file using a text editor, you may find these markers.
Suspicious Network Activity
Ransomware often communicates with command and control servers to receive instructions and transmit encryption keys. Monitoring your network for suspicious outbound traffic can help detect a ransomware infection.
Slow System Performance
Ransomware can consume system resources, causing your computer to slow down. If your computer’s performance significantly degrades without an apparent reason, it could be due to ransomware encryption processes running in the background.
Anti-Malware Alerts
A reliable anti-malware or antivirus program can often detect and alert you to ransomware activity. If your security software warns you about potential ransomware threats, take it seriously.
Conclusion
In conclusion, recognizing the signs of ransomware encryption is vital for a swift response to mitigate the damage. Staying informed about the latest ransomware threats and keeping your security software up to date is essential in the ongoing battle against cyber threats. Remember, prevention is the best defense, so regularly back up your files and follow best cybersecurity practices to reduce the risk of falling victim to ransomware attacks.


