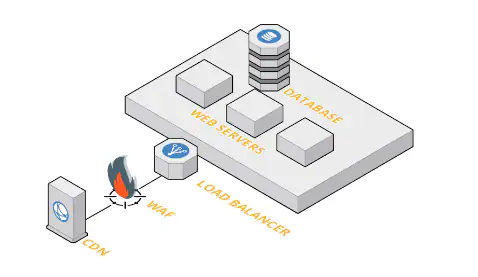
How to Get the Most Out of Palo Alto Networks Web Application Firewall Features?
Are you tired of constantly worrying about cyber threats attacking your web applications? Look no further than Palo Alto Networks Web Application Firewall (WAF). This powerful tool provides a comprehensive defense against attacks, but are you getting the most out of its features? In this blog post, we’ll dive into how to maximize the benefits of Palo Alto Networks WAF and keep your website safe from harm. Get ready to take your cybersecurity game to the next level!
Table of Contents
Configuring the Web Application Firewall
Managing Security Policies
Application and User Identification
Data Loss Prevention
Reporting and Analytics
Conclusion
Configuring the Web Application Firewall
Palo Alto Networks offers a web application firewall (WAF) feature to protect your web applications from attack. The WAF feature is available in all of the Palo Alto Networks next-generation firewalls. In this blog article, we will show you how to configure the WAF feature and get the most out of its capabilities.
The first thing you need to do is enable the WAF feature on your Palo Alto Networks firewall. This can be done from the Device > Setup > Services page in the web interface. Once you have enabled the WAF service, you need to create a security policy that will allow traffic from your trusted clients to reach the protected web server. To do this, go to Policies > Security and click Add. In theSource field, select the zone that contains your trusted clients. In the Destination field, select the zone that contains your web server. Under Service/URL Category, select http from the drop-down menu. Click OK to save your changes and apply the policy.
Now that your WAF policy is in place, you can begin configuring it to protect your web applications. The first thing you need to do is create a profile for each web application that you want to protect. To do this, go to Objects > Applications and click Add. Enter a name for your application and choose a protocol (http or https). If you are unsure which protocol to use, select https. Next
Managing Security Policies
When it comes to managing security policies, the Palo Alto Networks Web Application Firewall (WAF) provides some powerful features that can help you get the most out of your investment. Here are just a few of the things you can do with the WAF:
Create custom security policies tailored to your specific needs
Apply security policies across multiple devices and departments
Monitor and report on compliance with security policies
Enforce strong authentication and authorization measures
Control access to sensitive data and systems
With the WAF, you can create custom security policies that are tailored to your specific needs. This means that you can have different policies for different devices or departments, depending on their unique requirements. You can also monitor and report on compliance with these policies, so you can be sure that everyone is following them. Finally, the WAF gives you the ability to enforce strong authentication and authorization measures. This ensures that only authorized users have access to sensitive data and systems.
Application and User Identification
Palo Alto Networks web application firewall features provide granular control over web traffic and can be used to identify and block malicious traffic. Application and user identification is a key feature of the Palo Alto Networks web application firewall that allows admins to control access to specific applications and users. This section will discuss how to configure application and user identification on the Palo Alto Networks web application firewall.
The first step in configuring application and user identification is to create an Application object. To do this, go to Objects > Applications and click Add. Enter a name for the Application object and select the protocol(s) that will be used by the Application object. Next, add any URL categories that should be included in the Application object. Finally, click Save to apply the changes.
The next step is to create a User object. To do this, go to Objects > Users and click Add. Enter a name for the User object and select the type of user (e.g., Internal, External). Next, add any groups that should be included in the User object. Finally, click Save to apply the changes.
Once the Application and User objects have been created, they can be used in policies to allow or deny access to specific applications and users. For more information on how to create policies, see the documentation for your Palo Alto Networks device.
Data Loss Prevention
Palo Alto Networks’ web application firewall features can help prevent data loss by providing granular control over what traffic is allowed to enter and exit your network. By configuring the firewall to block specific types of traffic, you can ensure that only legitimate traffic is allowed through, and that any malicious or unauthorized traffic is stopped before it reaches your network. Additionally, the firewall can be configured to monitor and log all traffic passing through it, so that you can quickly identify and respond to any attempted data breaches.
Reporting and Analytics
Palo Alto Networks offers a comprehensive web application firewall feature set that provides users with granular control over their web applications. The web application firewall features include:
URL filtering: This allows administrators to block or allow access to specific URLs.
Content filtering: This allows administrators to block or allow access to specific types of content, such as images, videos, or Flash files.
Application profiling: This allows administrators to identify and block specific types of web application traffic, such as SQL injection attacks.
User authentication: This allows administrators to require user authentication before allowing access to a web application.
SSL/TLS encryption: This ensures that all traffic between the Palo Alto Networks firewall and the web server is encrypted.
Conclusion
Overall, Palo Alto Networks Web Application Firewall features offer a great way to protect your business from common threats. With the right security measures in place, you can rest assured that your data is secure and that any malicious attempts to access it will be blocked. The comprehensive options available through the Palo Alto web application firewall are sure to provide superior protection for businesses of all sizes. By following our tips above, you can get the most out of this powerful security feature and enjoy a greater degree of safety and peace of mind in knowing that your valuable resources are guarded against potential threats.



