August 2023
Protect Your Network: How Firewalls Defend Against Malicious Attacks?
In today’s digital age, security should be a top priority for individuals and businesses alike. With the increasing number of cyber threats, it’s essential to have reliable tools to safeguard your network from malicious attacks. That’s where firewalls come in – they act as a critical first line of defense against hackers and malware attempting […]
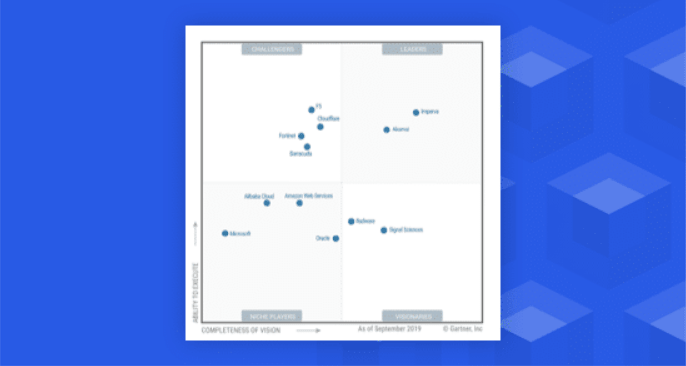
Navigating the Gartner Magic Quadrant for Web Application Firewalls: What You Need to Know
Welcome to the world of Gartner Magic Quadrant, where top-notch web application firewalls (WAFs) are evaluated and recognized for their excellence. If you’re a security professional who’s constantly looking out for ways to protect your organization from digital threats, then this post is definitely worth your time. In this article, we’ll take you through everything […]
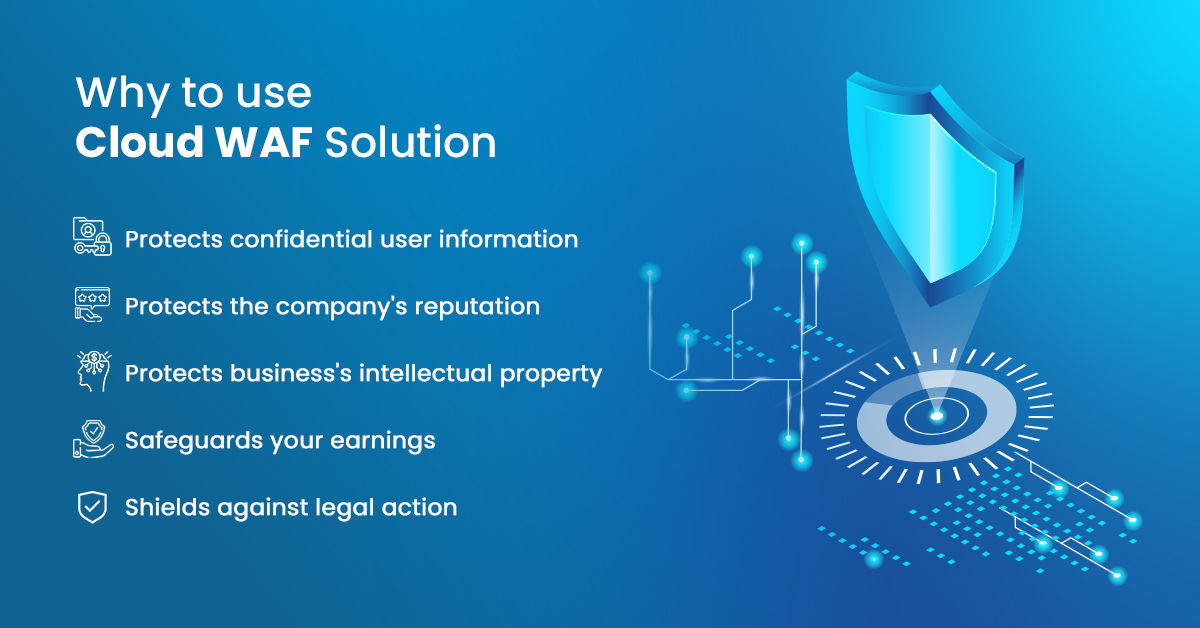
Why Your Business Needs a Cloud Web Application Firewall: Protecting Your Online Assets
Are you looking for an effective way to safeguard your online assets? Do you want to protect your business from cyber attacks and data breaches that can compromise sensitive information? Look no further than a cloud web application firewall (WAF). In today’s digital age, businesses of all sizes need robust security measures in place. A […]
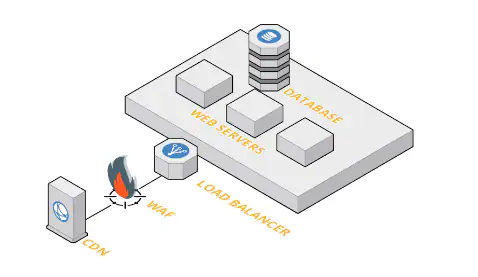
Comparing Top Players in the Web Application Firewall Market: Which One is Right for You?
Are you concerned about the security of your web applications? Do you want to protect your business from cyber threats and attacks? Look no further than a Web Application Firewall (WAF). But with so many options in the market, which one is right for you? In this blog post, we’ll compare top players in the […]
How to Get the Most Out of Palo Alto Networks Web Application Firewall Features?
Are you tired of constantly worrying about cyber threats attacking your web applications? Look no further than Palo Alto Networks Web Application Firewall (WAF). This powerful tool provides a comprehensive defense against attacks, but are you getting the most out of its features? In this blog post, we’ll dive into how to maximize the benefits […]
Ransomware and Cyber Extortion: Response and Prevention
Welcome to our latest blog post on the ever-growing threat of ransomware and cyber extortion. In today’s digital age, it’s become increasingly important for individuals and businesses alike to be aware of these insidious attacks that can leave you feeling helpless and vulnerable. From healthcare facilities to small startups, no one is immune from the […]
Ransomware: Defending Against Digital Extortion
Welcome to our latest blog post on ransomware! As the world becomes increasingly digital, cybercriminals are continuously finding new ways to exploit vulnerabilities in computer systems. One of the most significant threats facing businesses and individuals alike is ransomware – a type of malware that encrypts your files and demands payment in exchange for their […]
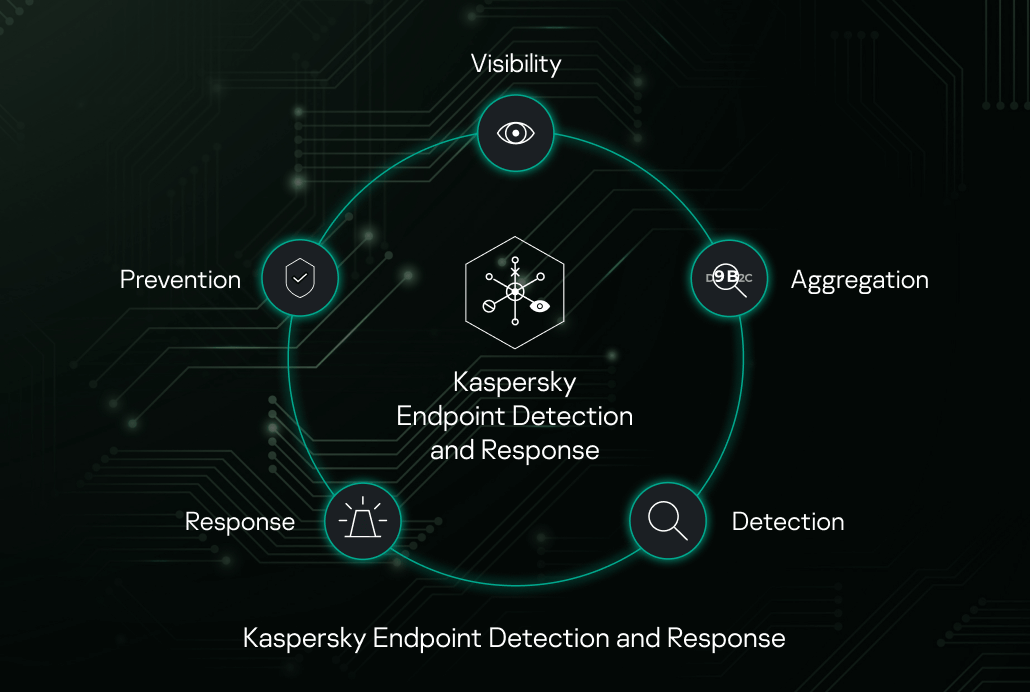
Why Endpoint Detection & Response (EDR) is Crucial for Your Cybersecurity Strategy?
In today’s digital age, cybersecurity is more important than ever before. With cyber threats becoming increasingly sophisticated and complex, businesses of all sizes are at risk of falling victim to a data breach. Endpoint Detection & Response (EDR) has emerged as a crucial component of any cybersecurity strategy that aims to keep hackers at bay. […]
Empowering Your Cybersecurity with Endpoint Detection and Response (EDR) Software
Introduction to Endpoint Detection and Response (EDR) Endpoint detection and response (EDR) software is a type of security solution that helps organizations detect, investigate, and respond to malicious activity on their endpoint devices. Endpoints are the devices that connect individuals and businesses to networks, such as laptops, desktops, servers, and mobile devices. EDR solutions are […]